|
It is using strong cryptography to protect traffic from eavesdropping and
optionally offering stronger authentication with DSA-keys (or RSA-keys in version 1).
Symmetric-key exchange as well as SSH server authentication is always done using DSA public
key encryption (or RSA-keys in version 1). For more detailed information about how the
ssh-protocol works and what benefits it provides, see [SSHFAQ].
The Secure Shell protocol is being standardised by the IETF (Internet
Engineering Task Force, http://www.ietf.org/), and there
are several independent implementations of the protocol.
You need to run a Secure Shell server on the machine you want to access
(Unix and VMS only), and you need to use a Secure Shell client on your local machine
(available on most platforms).
The actual version of the SSH protocol is 2 (SSH2).
There are quite a few implementations of SSH available (both commercial
and non-commercial).
Quite a few server implementations are planned, but only two seem to be
ready for production use. "SSH Secure Shell" of SSH Communications Security is a
commercial one, priced at USD 399 per server (see [SSHCOMSEC]). OpenSSH is a free version
of SSH developed by the OpenBSD project (see [OPENSSH]).
As we prefer open source software and there is no obvious difference in
functionality, we suggest to use OpenSSH. The document will concentrate on this server
implementation only.
Client implementations are available for virtually any platforms
(either native or in Java).
Many different ones are available. SSH Communications Security offers
one at USD 89 per client for Windows, Linux and Solaris. The Windows client is quite easy
to use and includes a graphical file transfer interface. OpenSSH includes clients for
remote access and file transfer, too (text based). Mindbright Technology offers a Java
implementation called MindTerm under the GNU license (see [MINDTERM]). A list of all free
implementations can be found at http://www.freessh.org/.
As Mindterm is written in Java - and can therefore be used on any
platform - we suggest to use this implementation, although it only supports SSH version 1
currently. The document will concentrate on this client implementation only.
This chapter explains how to install the chosen SSH server and client
implementations
(see previous chapter).
It is possible to install OpenSSH on almost every Unix implementation.
OpenSSH requires zlib and OpenSSL.
zlib
If zlib is already installed on your server, skip this chapter.
Put the distribution into a temporary directory (see Table 3for
information on where to get it) and follow the instructions below (you might want to
specify additional options when running configure).
> gunzip <distribution>.tar.gz
> tar xvf <distribution>.tar
> cd <distribution>
> ./configure
> make
> su
> make install
> exit
OpenSSL
If OpenSSL is already installed on your server, skip this
chapter.
Put the distribution into a temporary directory (see Table 3for
information on where to get it) and follow the instructions below (you might want to
specify additional options when running config).
> gunzip <distribution>.tar.gz
> tar xvf <distribution>.tar
> cd <distribution>
> ./config
> make
> su
> make install
> exit
OpenSSH
Put the distribution into a temporary directory (see Table 3for
information on where to get it) and follow the instructions below (you might want to
specify additional options when running configure).
> gunzip <distribution>.tar.gz
> tar xvf <distribution>.tar
> cd <distribution>
> ./configure --sysconfdir=/etc/ssh
> make
> su
> make install
> make host-key
> exit
Running make host-key creates the RSA (for version 1
connections) and DSA (for version 2 connections) keys. They get stored in the
sysconfdir.
As MindTerm is written in Java, you can install and run it on virtually
every platform. You might even want to run it as an applet, this requires the
installation on the server (follow the instructions in the chapter MindTerm as Applet
below).
Extract the distribution into a new directory (see Table 3for
information on where to get it). We recommend a subdirectory (called mindterm) of the
common program installation location (such as /usr/local/ on Unix platforms or \program
files\ on Windows).
MindTerm runs with any Java Runtime Environment (JRE) higher or equal
as version 1.1. See Table below for addresses about where to get and how to install a JRE
for your platform.
 Configuration
Configuration
The configuration of OpenSSH is done in the file sshd_config. It is
located in the directory /etc/ssh, or whatever you specified with the sysconfdir option
when installing the software.
The default option settings should be fine. They allow password or key
authentication. You might want to enable X11 forwarding. See the sshd manual page for
more information about the options.
If you are using Pluggable Authentication Modules (PAM), you will need
to manually install a PAM control file as /etc/pam.d/sshd (or wherever your system
prefers to keep them). A generic PAM configuration is included as
contrib/sshd.pam.generic within the distribution of OpenSSH, you may need to edit it
before using it on your system. If you are using a recent version of Redhat Linux, the
config file in contrib/redhat/sshd.pam should do the job.
Make sure the mindtermfull.jar file is included in your CLASSPATH
environment variable.
Examples of how to embed the applet in a HTML page can be found at the
address where you downloaded MindTerm (see Table 3).
To allow connections to other servers than the one providing the
applet, to create ssh-tunnels and to access the local file system, you need to sign the
applet. A tutorial can be found at http://www.securingjava.com/appdx-c/.
 Invocation
Invocation
First of all, you will have to start the server process. It is
recommended to include this in
your system startup scripts.
> su
> sshd
> exit
Now, you can start MindTerm on your client.
> java mindbright.application.MindTerm
You might want to use javaw instead of java on a Windows client as this
does not open a
dummy console window.
This opens the MindTerm terminal window.
Check that password authentication is set (Settings/SSH Connection).
Enter the name or IP-address of the server you want to connect to at the
SSH Server/Alias: prompt. MindTerm will ask you for an alias name to store the settings.
The next time you connect, you can only specify this alias.
You get prompted for the login name.
Because this is the first time you connect to this host, MindTerm asks
you whether it should add the host to the set of known hosts. You should answer this with
Yes, as it will allow MindTerm to store the public key of the host and compare it to the
one the host provides on each connect (making sure you get where you want).
You get prompted for your password.
All communication - including the authentication procedure - is
encrypted. For detailed information about the SSH protocol, please see [IETF].
Preparation
In order to authenticate yourself with a key, you will - of course -
need to have a key. Generate your key-pair (private and public) using the Create RSA
Identity... in the File menu. Move the mouse within the text field at the top until the
progress bar shows 100%. Specifiy the Keylength (1024 should be ok), the name of the key
files, a password (pass-phrase, use a 20 to 30 character sentence, avoiding prosa) and a
comment. Later on, the comment will be used to prompt you for the password (pass-phrase).
Choose Generate.
Two files have been generated. One with the filename you have specified
that contains your private key, and one with the same name and the extension .pub that
contains the public key.
It is very important to make sure that the private key can only be read
by you.
To use the key, you must transfer the .pub public key file to the SSH
servers you want to use and add the contents of it as a line to the file authorized_keys
in the ssh directory ~/.ssh of the user you want to connect as. For convenience, MindTerm
copies your public key to the clipboard.
The steps up to here need only to be taken once. For all subsequent
logins, you need to follow the steps below only.
Getting the Connection
Check that RSA key authentication, the proper key filename and host is
set (Settings/SSH Connection). Remember that MindTerm does currently support SSH version
1 (and therefore RSA key authentication) only.
MindTerm will ask you for an alias name to store the settings. The next
time you connect, you can only specify this alias.
If you did not specify a user name in the settings, you will get
prompted now.
Then you will have to specify the password (pass-phrase) of your key
(if you failed to upload it to server before, MindTerm will issue an error message).
And if all information you have provided is correct - you're logged
in!
 Tunnelling
Tunnelling
Using SSH, you have the possibility to tunnel any protocol. A tunnel
connects a port of the local machine to a port on a remote machine, via the SSH protocol
and ports.
You can for example create an ftp-tunnel that connects port 5521 on your
local machine to the ftp port (21) on a remote machine. Then you can connect to port 5521
on your local machine using any ftp client - this will actually connect you (indirectly,
but completely transparent) to port 21 on the remote machine. And the complete
communication is encrypted!
In MindTerm, you can set up tunnels using the option Basic... or
Advanced... in the Tunnels menu.
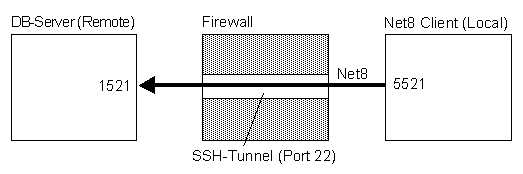
One common problem with SQL*Net and Net8 is, that in most cases they are
not allowed through firewalls. The common ports 1521 for Net8 are often blocked. One very
elegant solution for this problem is to use the Secure Shell Tunnel
mechanism.
You can for example create an Net8-tunnel that connects port 5521 on your
local machine to the Net8 port (1521) on a remote machine. Then you can connect to port
5521 on your local machine using any Net8 client - this will actually connect you
(indirectly, but completely transparent) to port 1521 on the remote machine. And the
complete communication is encrypted. Often you have to set the IP-Adress in the
LISTENER.ORA file.
 X11
Forwarding X11
Forwarding
Provided that your SSH server has X11 Forwarding set on and you have an X
server running on your local machine, you can even display X11 through the SSH
connection.
The SSH server will set your DISPLAY environment variable when
connecting. It will be set to <servername>:<some_high_number>:0. The SSH server
will then forward the X11 protocol to your local X server that you have specified in the
settings (see More options... in the SSH Connection... option of the Settings menu).
 How to install the popular SSH client TeraTermPro & TTSSH ? How to install the popular SSH client TeraTermPro & TTSSH ?
Tera Term Pro, written by T.Teranishi is a popular TELNET
client for MS windows. However Tera Term Pro does not come with native SSH support. Robert
O'Callaham wrote an excellent SSH extension for it. Here are the URL's to download Tera
Term Pro and TTSSH.
 Secure Copy Remote File Program: scp Secure Copy Remote File Program: scp
The SSH utility scp copies
files between hosts on a network. It uses ssh for data
transfer, and uses the same authentication and provides the same security as ssh. Unlike rcp , scp will ask for passwords or passphrases if they are needed for
authentication.
Any file name may contain a host and user specification to
indicate that the file is to be copied to/from that host. Copies between two remote hosts
are permitted.
Example: Copy remote file: oracle.tar to local
directory.
$ scp zahn@remotehost.domain.com:/home/zahn/oracle.tar
.
zahn@remotehost.domain.com's password: ....
Example: Copy local file: oracle.tar to remote
directory /home/zahn.
$ scp oracle.tar
zahn@remotehost.domain.com:/home/zahn
zahn@remotehost.domain.com's password: ...
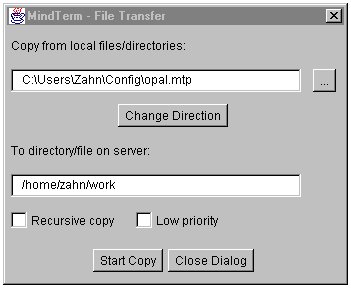
The same functionality as the described scp Unix utility offers the free java program MindTerm (see our
article: Installing and using Secure Shell SSH).
Click "File", "SCP File Transfer ..." as displayed in the screenshot below.
 FTP Tunneling (Port Forwarding) using SSH FTP Tunneling (Port Forwarding) using SSH
Using SSH (Secure Shell), you have the possibility to tunnel
any protocol. A tunnel connects a port of the local machine to a port on a remote machine,
via the SSH connection. Tunneling is often called Port Forwarding. Using this
technique you may access a FTP-Server behind a firewall in the DMZ (Demilitarized Zone) or
even in the HSZ (High Secure Zone). The following prerequisite must be established:
-
The firewall is open for the SSH Port 22
-
There is a SSH-Server behind the firewall
-
The FTP-Server in the DMZ or HSZ must be known by the
SSH-Server
You can enable secure connections over the internet using
any application protocol, like ftp, telnet, sqlnet, etc. It sounds quite complex, but it is
simple. Let's look at an example. The setup is as follows: You have a client that is
connected to the internet. The FTP-Server you want to access via ftp is in a corporate LAN
(HSZ), behind a firewall. The firewall does only allow the SSH protocol (port 22), you have
access to the SSH-server.
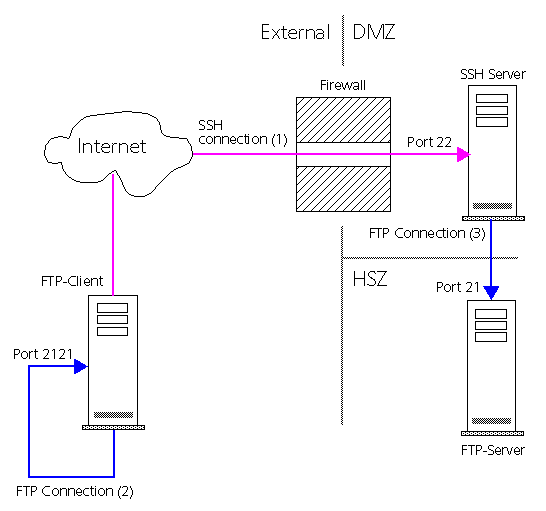
-
Establish an SSH connection from the FTP-Client to the
SSH-Server (1). The SSH port (22 by default) has to be allowed on the firewall. The
following screenshot shows how to establish an SSH connection in MindTerm
-
Enable ftp PORT and localhost 127.0.0.1 in the SSH
Settings of Mindterm.
-
Define a tunnel from port 2121 on the FTP-Client to port
21 on the FTP-Server. The following screenshot shows how to create tunnels in
MindTerm.
-
Enable PASV-Mode in your FTP-Tool, we use Leech FTP.
-
Now you are ready to establish the (logical) ftp
connection (2) to the FTP-Server. Enter 2121 in the field Port and localhost in the
field Host or URL. Leech FTP will now connect to the FTP-Server through the
SSH-Server.
Your FTP-client listens on port 2121 and forwards all
communication through the already established SSH connection to the SSH-Server. This part
of the communication is encrypted and appears as SSH communication on the network. The
SSH-Server establishes a connection to port 21 on the FTP-Server (3). It decodes the
SSH communication and forwards the ftp commands there (Port Forwarding). This part is not
encrypted, it appears like normal ftp communication on the network. By physically
connecting to port 2121 on your local machine using any ftp client you actually connected
logically to port 21 on the remote machine iindirectly, but completely transparent !
 Appendix
Appendix
|
Abbreviation
|
Meaning
|
|
ftp
|
File transfer protocol.
|
|
IETF
|
Internet Engineering Task Force, http://www.ietf.org/.
|
|
rexec
|
Remote execution.
|
|
rsh
|
Remote shell.
|
|
SSH
|
Secure SHell.
|
|
WWW
|
World Wide Web.
|
|
Abbreviation
|
Location
|
|
IETF
|
http://www.ietf.org/
|
|
OPENSSH
|
http://www.openssh.com/
|
|
SSHCOMSEC
|
SSH Communications Security, Internet Portals, http://www.ssh.org/
and http://www.ssh.com/.
|
|
SSHFAQ
|
http://opensores.thebunker.net/pub/mirrors/ssh-faq/ssh-faq.html
|
|

![]() Overview
Overview![]() Introduction
Introduction![]() Secure
Shell
Secure
Shell






