![]() How to connect 2 ... n SSH Tunnels ?
How to connect 2 ... n SSH Tunnels ? ![]()
Security in one of the most important demands in today's Internet environment. One common approach to secure the personal or IT infrastructure is to use a two wall barrier or firewall. The first wall protects the DMZ (Demilitarized Zone) from the Internet, the second wall protects the HSZ (High Security Zone) from the DMZ and Internet. A tighten security environment often results in a more complicated working area, where some services like FTP or TELNET cannot be used anymore. SSH offers some possibilities to facilitate the daily working, in this Tip we want to show how to access an Oracle Database behind a two barrier firewall where only Port 22 for SSH is opened for authenticated access from remote.
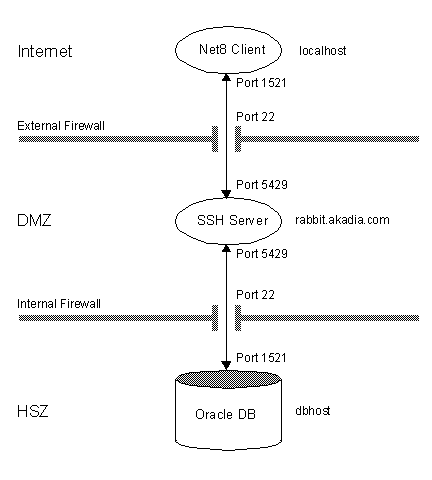
Requirements
-
Port 22 must be opened on external Firewall
-
Port 22 must be opened on internal Firewall
-
You can login to the SSH Server and the internal DB Server
Steps to perform
1. Create the "external" SSH Tunnel from the localhost to the SSH Server
2. Create the "internal" SSH Tunnel from the SSH Server to the DB Server
3. Connect your Client (e.g. SQLPLUS) to the DB-Server
1. Create the "external" SSH Tunnel from the localhost to the SSH Server
-
Login to the SSH Server using MindTerm, TeraTerm or any SSH Client with your personal Account, you will reach the Shell Prompt of this machine.
-
Create an SSH Tunnel from Port 1521 on localhost to an unprivileged Port 5429 on the SSH Server. This can be accomplished within the SSH Client (Tunnels, Basic).
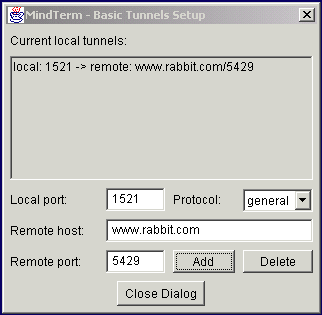
-
Enable "GatewayPorts yes" for the DB Server in the global SSH Configuration File which can be found in /etc/ssh/ssh_config or in your local SSH Configuration File $HOME/.ssh/config.
####### Settings for Host dbhost
#
Host dbhost*
####### GatewayPorts
#
# Specifies whether remote hosts are allowed
# to connect to local forwarded ports. The argument
# must be "yes" or "no". The default # is "no".
#
GatewayPorts yes
2. Create the "internal" SSH Tunnel from the SSH Server to the DB Server
-
Login to the DB Server SSH Server using your current Terminal Emulation with the following Command which opens the "internal" SSH Tunnel from the unprivileged Port 5429 on the SSH Server to Port 1521 on the DB Server. Usually Port 1521 is used for Oracle Net8 Connections, if you are not sure, ask your DB Administrator for this Port.
$ ssh -L 5429:dbhost:1521 dbhost
Both Tunnels are now connected and ready to use !
-
You can add the above command to create the "internal" tunnel permanently in the SSH Configurationfile, then you can just login to the dbhost with:
$ ssh dbhost
###### LocalForward
#
# Specifies that a TCP/IP port on the local machine
# be forwarded over the secure channel to given host:port
# from the remote machine. The first argument must be a
# port number, and the second must be host:port. Multiple
# forwardings may be specified, and additional forwardings
# can be given on the command line. Only the superuser can
# forward privileged ports.
#
LocalForward 5429 dbhost:1521
3. Connect your Client (e.g. SQLPLUS) to the DB-Server
You have to setup your local TNSNAMES.ORA File for SQLPLUS with the following entry:
ORA1.world = (DESCRIPTION = (ADDRESS
= (COMMUNITY = tcp.world)
(PROTOCOL = TCP)
(Host = localhost) (Port = 1521))
(CONNECT_DATA =
(SID = ORA1) (GLOBAL_NAME = ORA1.world)
(SERVER =
DEDICATED)))
Test the connection with TNSPING and connect to the DB Server
ARKUM:zahn> tnsping ORA1
Attempting to contact (ADDRESS=(COMMUNITY=tcp.world)
(PROTOCOL=TCP)(Host=localhost)(Port=1523)) OK (310 msec)
ARKUM:zahn> sqlplus scott/tiger@ORA1
Connected to:
Oracle8i Enterprise Edition Release 8.1.7.0.0 - Production
With the Partitioning option
JServer Release 8.1.7.0.0 - Production
SQL>
This example shows how to connect two SSH Tunnels, but you can connect any number of SSH Tunnels, the only requirement is, that you can logon to all intermediated and final servers over a secure connection like SSH.